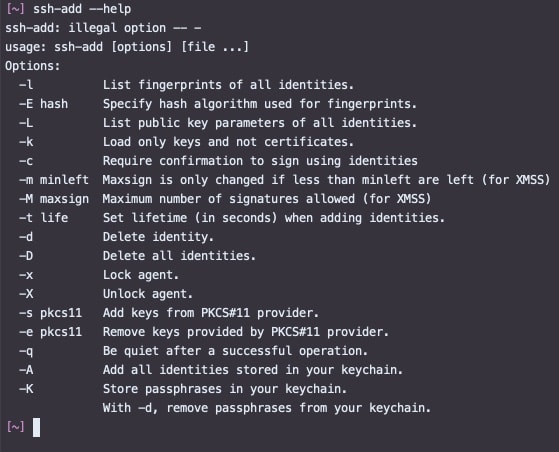
If the remote system is not configured to support password-based authentication, you will need to ask system administrators to add your public key to the /.ssh/authorizedkeys file in your account (if your account doesn't have /.ssh/authorizedkeys file, system administrators can create one for you). Jun 15, 2015 Support Communities / Mac OS & System Software / OS X. You put the.pub file on the remote system into the.ssh/authorizedkeys file of the destination account. In your case that would be. Able to decrypt something from the sender using the sender's public key that the receiver allowed to be put into.ssh/authorizedkeys is how the. May 28, 2006 In my example, the server is a Linux system. Any other UNIX running OpenSSH will do fine. First, we copy the key from your Mac to the server using SCP: client: user$ scp /.ssh/idrsa.pub user@server.example.com: This will put the key in your homedir. Next, we SSH to the server, and add our key to the list of authorized keys.
Keychain Access User Guide
If you migrate your data to a different Mac using Setup Assistant, your keychain are automatically transferred to the new computer.
If you didn’t use Setup Assistant, the best way to copy your keychains to a new computer is to export and then import them using Keychain Access. See Import and export keychain items.
However, you can also manually copy your keychains to another Mac using the steps below.
Macos Authorized Keys For System Accounts Manager
On your Mac, locate the keychain files you want to transfer.
Keychains are usually located in the Keychains folder in the Library folder in your home folder. To locate these files, press and hold the Option key and choose Go > Library, then open the Keychains folder.
Select the keychains you want, then press and hold the Option key and drag the selected keychains into another folder to copy them to the folder.
Keychain files typically end with .keychain-db. Don’t select and copy encrypted folders with names that appear as a series of numbers.
Transfer the folder containing the keychains to the new computer.
Important: Transfer the keychains in a safe manner so no unauthorized person can access them. For example, use AirDrop or a USB flash drive to copy the files.
Change the name of the transferred keychains on your new computer so they don’t become confused with any of the existing keychains.
This is especially important if you are copying a standard keychain, such as the login keychain.
Open Keychain Access, located in the Utilities folder in the Applications folder.
Add each copied keychain one by one by choosing File > Add Keychain, selecting your keychain, then clicking OK.
Important: Be sure not to leave your keychain on any computer that is not secure. Doing so may allow other users to access items with your keychain.
To access the items in the keychain on the new computer, you must use the same password you used for the keychain on the previous computer.
Note: You can’t copy passwords stored in your iCloud keychain. To transfer these keychain items to another computer, set up iCloud keychain on the other computer using your iCloud user name and password.
Macos Authorized Keys For System Accounts Online
The LocalSystem account is a predefined local account used by the service control manager. This account is not recognized by the security subsystem, so you cannot specify its name in a call to the LookupAccountName function. It has extensive privileges on the local computer, and acts as the computer on the network. Its token includes the NT AUTHORITYSYSTEM and BUILTINAdministrators SIDs; these accounts have access to most system objects. The name of the account in all locales is .LocalSystem. The name, LocalSystem or ComputerNameLocalSystem can also be used. This account does not have a password. If you specify the LocalSystem account in a call to the CreateService or ChangeServiceConfig function, any password information you provide is ignored.
A service that runs in the context of the LocalSystem account inherits the security context of the SCM. The user SID is created from the SECURITY_LOCAL_SYSTEM_RID value. The account is not associated with any logged-on user account. This has several implications:
- The registry key HKEY_CURRENT_USER is associated with the default user, not the current user. To access another user's profile, impersonate the user, then access HKEY_CURRENT_USER.
- The service can open the registry key HKEY_LOCAL_MACHINESECURITY.
- The service presents the computer's credentials to remote servers.
- If the service opens a command window and runs a batch file, the user could hit CTRL+C to terminate the batch file and gain access to a command window with LocalSystem permissions.
Macos Authorized Keys For System Accounts 2017
The LocalSystem account has the following privileges:
- SE_ASSIGNPRIMARYTOKEN_NAME (disabled)
- SE_AUDIT_NAME (enabled)
- SE_BACKUP_NAME (disabled)
- SE_CHANGE_NOTIFY_NAME (enabled)
- SE_CREATE_GLOBAL_NAME (enabled)
- SE_CREATE_PAGEFILE_NAME (enabled)
- SE_CREATE_PERMANENT_NAME (enabled)
- SE_CREATE_TOKEN_NAME (disabled)
- SE_DEBUG_NAME (enabled)
- SE_IMPERSONATE_NAME (enabled)
- SE_INC_BASE_PRIORITY_NAME (enabled)
- SE_INCREASE_QUOTA_NAME (disabled)
- SE_LOAD_DRIVER_NAME (disabled)
- SE_LOCK_MEMORY_NAME (enabled)
- SE_MANAGE_VOLUME_NAME (disabled)
- SE_PROF_SINGLE_PROCESS_NAME (enabled)
- SE_RESTORE_NAME (disabled)
- SE_SECURITY_NAME (disabled)
- SE_SHUTDOWN_NAME (disabled)
- SE_SYSTEM_ENVIRONMENT_NAME (disabled)
- SE_SYSTEMTIME_NAME (disabled)
- SE_TAKE_OWNERSHIP_NAME (disabled)
- SE_TCB_NAME (enabled)
- SE_UNDOCK_NAME (disabled)
Macos Authorized Keys For System Accounts Online
Most services do not need such a high privilege level. If your service does not need these privileges, and it is not an interactive service, consider using the LocalService account or the NetworkService account. For more information, see Service Security and Access Rights.